🔓Data Compliance
Overview
Both from an ethical standpoint and a compliance/policy standpoint, we are obliged to ensure that we handle data in an appropriate manner. The way in which we handle data — including where it's stored, how it's stored, whom it's shared with, and how long it's retained — depends on the data type, as listed below. In the following sections, PII refers to Personally Identifiable Information, such as emails, names, addresses, etc.
Jurisdiction
TEDxIndianaUniversity must comply with Indiana University and Indiana University Bloomington data policy. Additionally, we may be required to comply with State and Federal data regulations. At this time, TEDxIndianaUniversity is not obliged to comply with GDPR (European Union General Data Protection Regulation), which applies to larger companies and organisations operating in the EU or the EEA. Additionally, we do not yet qualify as an organisation that must comply with other US State data regulation, such as CCPA (California Consumer Privacy Act). That being said, TEDxIndianaUniversity may use practices and/or tools traditionally used with GDPR or CCPA to comply with University policy, where required.
When in doubt, always consult the Data Sharing and Handling tool to determine what kind of data you're processing or storing. Some data levels will require that you take preventative measures and protect data in Microsoft365.
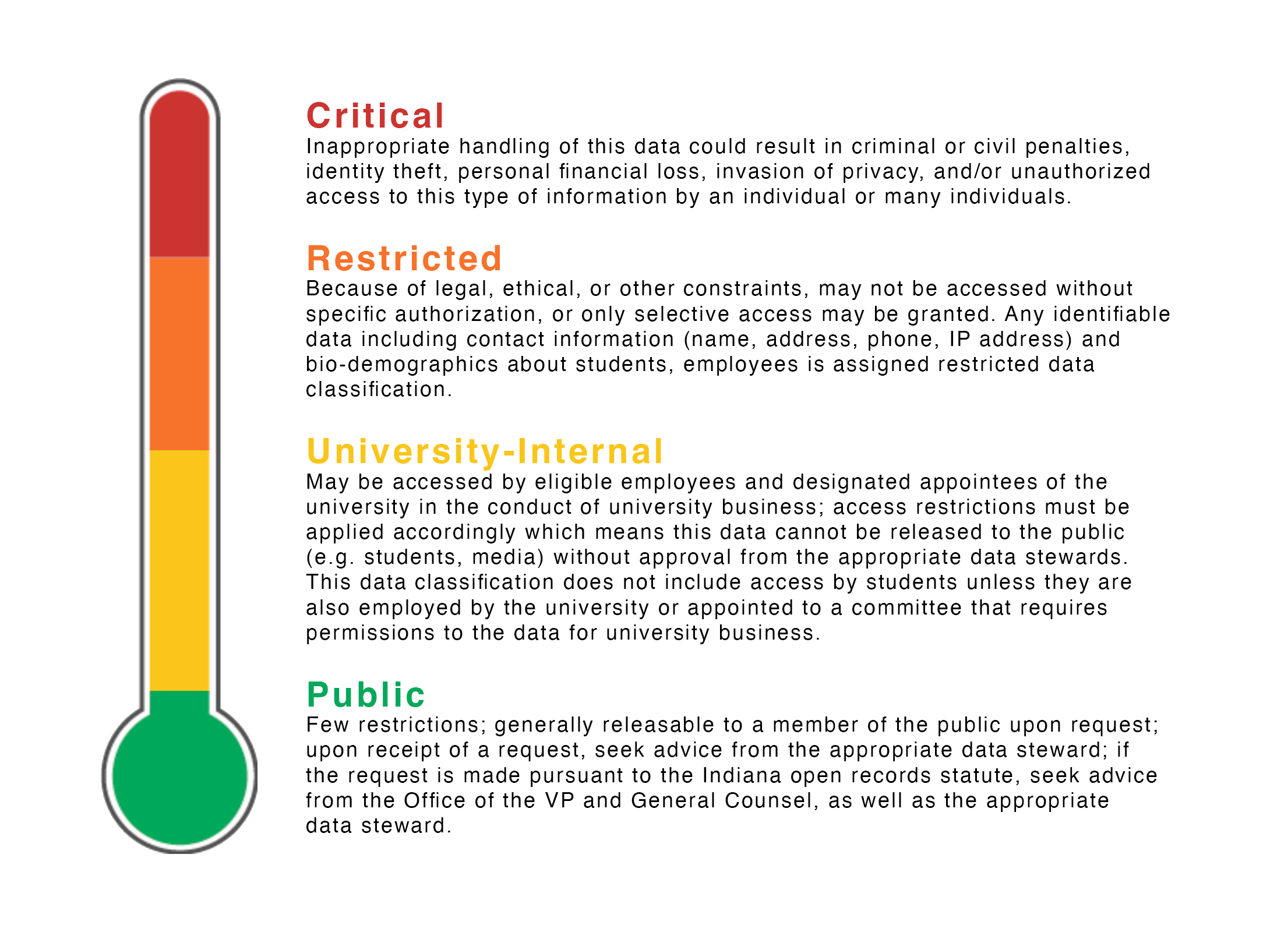
University Public Data
Some of our data exists within the bounds of University Public Data, which has no special processing requirements. Examples of Public Data include generally available event information and public PII, such as names, emails, and usernames. See more: What is public data?
University Internal Data
We also process a good deal of University Internal Data, which should not be published to public sites and should remain on University systems (such as Microsoft365). Internal Data includes non-public PII, such as phone numbers. It also includes physical security concerns, such as internal floor plans. See more: What is University-internal data?
University Restricted Data
We also process some University Restricted Data. This data in no means should leave University systems, and access controls should be closely monitored to ensure that no additional party — other than those working directly with the information — may access it. This includes student academic transcripts, class schedule, date of birth, gender, pronouns, home address, and more. Please consult What is restricted data? and the Data Sharing and Handling tool to determine if the data you are using is considered Restricted. If you are using, processing, or storing Restricted data, you MUST COMPLY with protective measures in Microsoft365. Additionally, per TEDxIndianaUniversity policy, you must name folders with Restricted data in this convention: TEDxRESTRICTED-{topic/name}such as TEDxRESTRICTED-HighSchoolGPAs
University Critical Data
Although unlikely, it is possible that we may process or store University Critical Data, such as passport or visa information, state ID information, or credit card information. Learn more about what is considered Critical Data. Like Restricted data, you MUST COMPLY with protective measures in Microsoft365. If the data isn't something you'd normally give out to a friend, it is likely Critical data; always check the Data Sharing and Handling tool to ensure you understand your obligations. Additionally, per TEDxIndianaUniversity policy, you must name folders with Critical data in this convention: TEDxCRITICAL-{topic/name}such as TEDxCRITICAL-SpeakerVisa. You are also required to monitor and strengthen access controls to permit the minimum number of parties required. If you are finished with the data, delete the information... and then delete it from the trash or recycle permanently. For Critical data, avoid using traditional email or messaging for sharing or collecting the files. Instead, consider using IU Secure Share.
Microsoft Storage at IU is approved for PHI/critical data classifications with a few notable exceptions below.
NOT approved for:
Credit card and Payment Card Industry (PCI) data
Export controlled research data
Controlled Unclassified Information (CUI)
Advancement donor gift agreements and wealth information
Last updated